Overview
Your organization’s most valuable asset is its data and the users who have access to it — but you’re only as secure as your user workstations. Collecting, storing and analyzing all user and privileged account data generally requires large amounts of storage, time-consuming collection of event data and in-house expertise about the event log data collected. That’s where we come in.
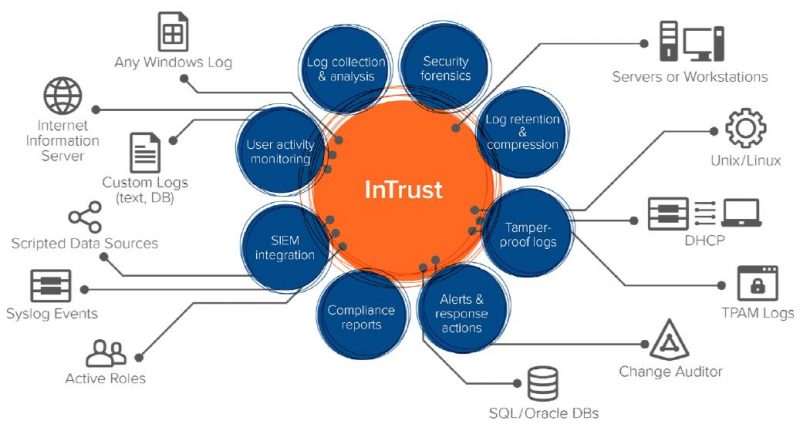
Quest InTrust is smart, scalable event log management software that lets you monitor all user workstation and administrator activity from logons to logoffs and everything in between. Slash storage costs with 20:1 data compression, and store years of event logs from Windows, UNIX/Linux servers, databases, applications and network devices. InTrust real-time log monitoring and alerting enables you to immediately respond to threats with automated responses to suspicious activity.
Source: Quest
Key capabilities
Central log collection
Simplified log analysis
Consolidate cryptic event logs from disparate sources into a simple, normalized format of who, what, when, where, where from and whom to help you make sense of the data. Unique, full-text indexing makes long-term event data easily searchable for fast reporting, troubleshooting and security investigation.
SIEM integration
InTrust delivers easy and reliable integration with Splunk, QRadar, ArcSight and any other SIEM supporting common Syslog formats (RFC 5424, JSON, Snare). With InTrust’s predictable per-user license model, you can collect and store as much data as you need for as long as you want. Then use pre-built filters based on industry best practices to forward only relevant log data and alerts to your SIEM solution for real-time, security analytics. This integration enables you to slash your annual SIEM licensing costs.
Event log compression
Collect and store years of data in a highly-compressed repository, 20:1 with indexing and 40:1 without, so you can save on storage costs by up to 60%, satisfy data retention policies and ensure continuous compliance with HIPAA, SOX, PCI, FISMA and more.
Alerting and response actions
Tamper-proof protocols
Source: Quest
Tour
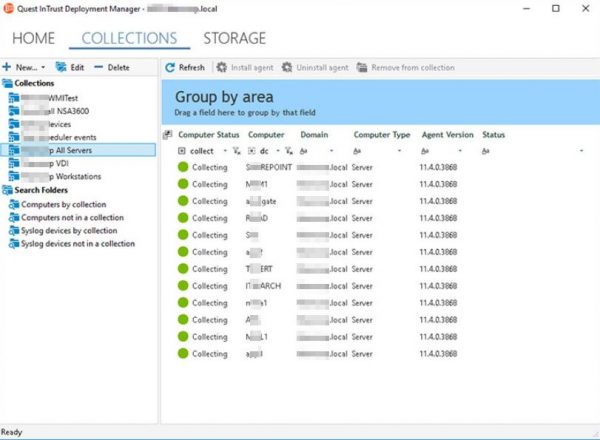
- Real-time log collection
- Pre-defined searches
- SIEM event forwarding
- Unix/Linux log management
- Syslog Parsing
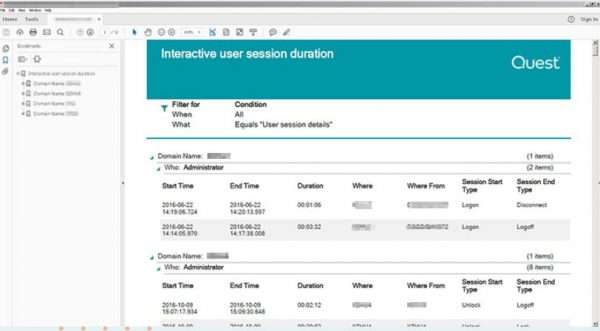
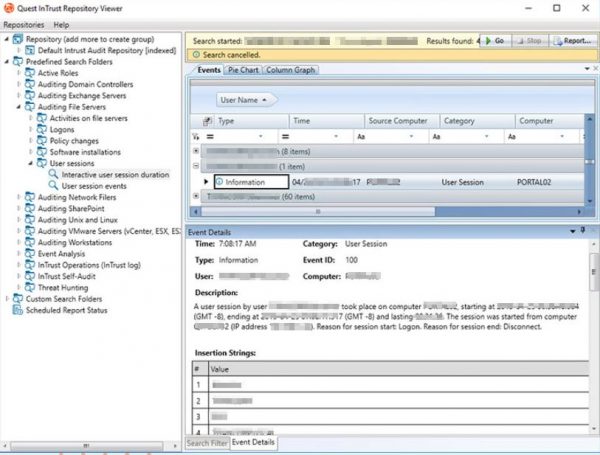
- Interactive user sessions
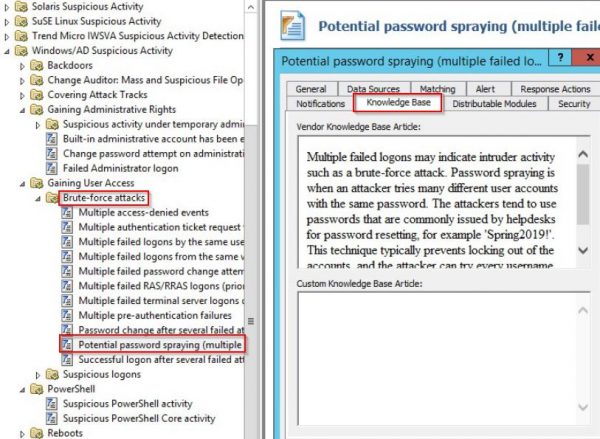
- Password spray alerts
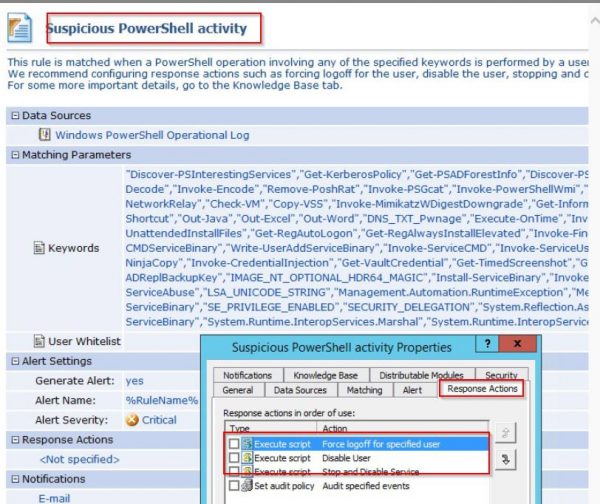
- PowerShell Monitoring
- Dynamic operators
- Export built-in reports
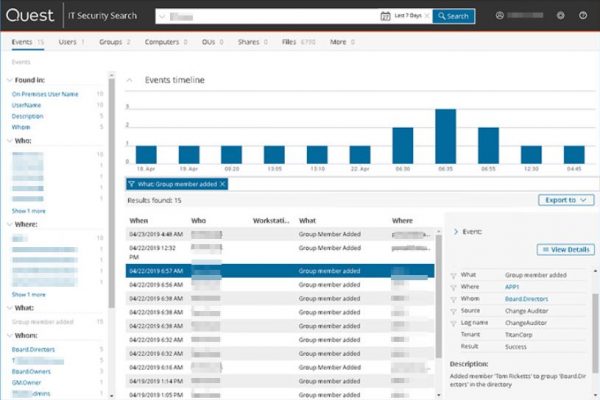
- IT Security Search
Automate real-time gathering of event logs from a single console with our event log management software.
Use pre-defined searches to zero in on critical event data with our log monitoring tool.
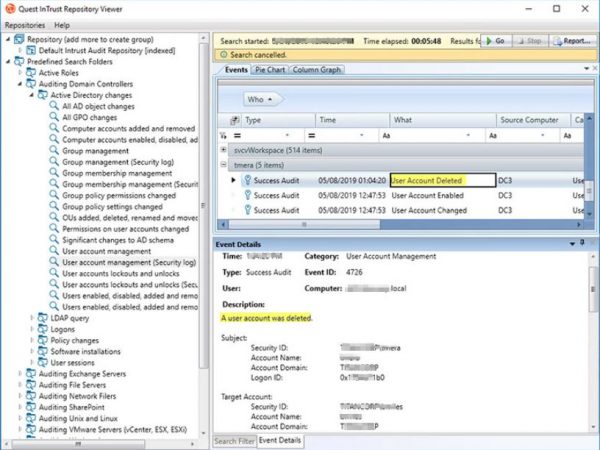
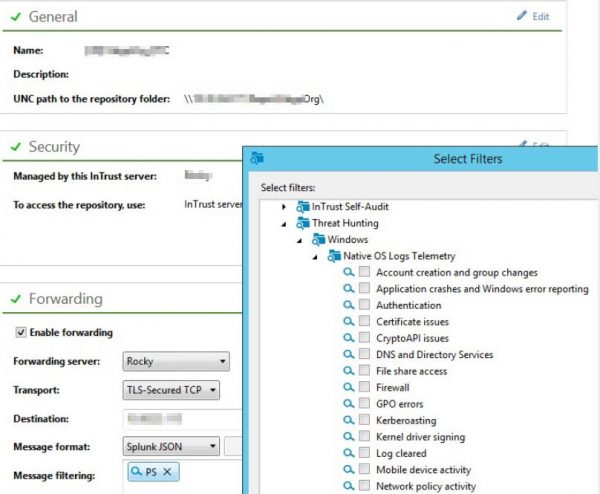
Use best practice filters to selectively forward only relevant data to your SIEM to reduce costs, minimize event noise and improve threat hunting efficiency and effectiveness.
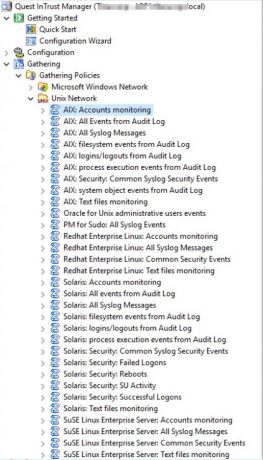
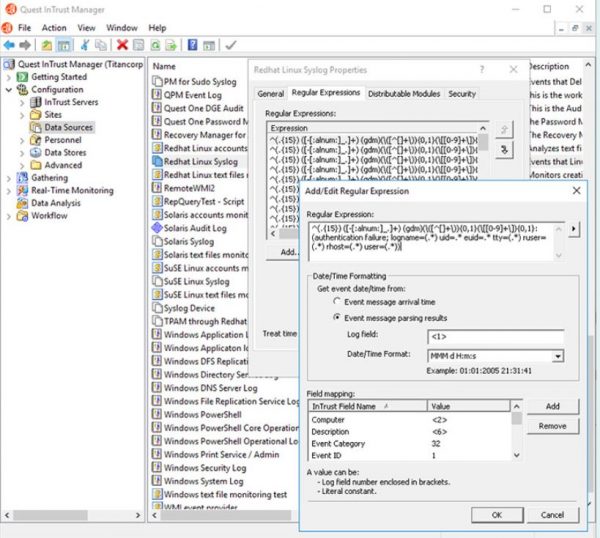
Send email notifications to specific users and their managers with our log monitoring tools.

Export built-in reports for troubleshooting and review.